Malicious Chrome Extensions Stealing Data: What You Need to Know [2025]
A few weeks ago, security researchers uncovered something that should make every Chrome user sit up and pay attention. Two browser extensions were quietly siphoning data from over 170 high-value websites, and millions of people had no idea they were infected. According to WebProNews, these extensions were known as Phantom Shuttle.
The scary part? These weren't obvious malware. They looked legitimate. They came with a price tag, professional descriptions, and claimed to be proxy services. They'd been sitting in the Chrome Web Store since 2017.
This isn't a one-off incident. Browser extensions represent one of the biggest blind spots in cybersecurity right now. While your antivirus scans files and your firewall blocks network threats, most people don't think twice about what permissions they're granting to add-ons. And that's exactly why attackers love them.
In this guide, I'll walk you through exactly what happened with Phantom Shuttle, how these attacks work, and most importantly, what you need to do to protect yourself. Because the truth is, if you're using Chrome, you're probably at risk right now.
TL; DR
- The Attack: Two extensions called Phantom Shuttle rerouted traffic through compromised proxies and harvested credentials from 170+ high-value sites including developer platforms, cloud services, and social media, as detailed by The Hacker News.
- The Scale: Over 4.3 million users installed malicious extensions across Chrome and Edge browsers, as reported by Infosecurity Magazine.
- The Detection: Security researchers identified the extensions by analyzing network traffic patterns and anomalous data exfiltration behavior, as explained by Cybersecurity News.
- The Risk: Browser extensions remain a critical security vulnerability because users rarely audit their permissions or monitor their behavior.
- Your Action: Audit installed extensions immediately, remove anything you don't recognize, and be extremely selective about what permissions you grant to new add-ons.
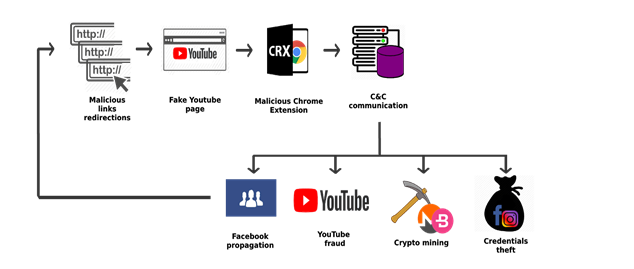

The Phantom Shuttle attack primarily targeted developer platforms and cloud services, each comprising 20% of the total targets. Other significant targets included social media, adult content, financial platforms, and email services, each accounting for 15%. Estimated data based on described attack strategy.
Understanding the Phantom Shuttle Attack
What Phantom Shuttle Actually Did
Phantom Shuttle wasn't trying to steal your email password or your banking credentials directly. That would've been too obvious and would've triggered security warnings. Instead, it was designed to intercept traffic heading to specific high-value targets. The attackers were playing a numbers game. They knew that if they could redirect traffic from thousands of users heading to developer platforms, cloud service consoles, and social media sites, some percentage of those users would be authenticated. That means cookies, session tokens, API keys, and other sensitive credentials would flow right through their compromised proxy servers.
Think of it like setting up a toll booth on a highway. Most cars pass through empty, but occasionally you get a delivery truck carrying valuable cargo. You don't need to rob every vehicle. You just need to watch the traffic go by and grab what's valuable.
The extensions operated by monitoring outgoing network traffic and listening specifically for requests to about 170 domains. The researchers identified targets including:
- Developer platforms and code repositories
- Cloud service management consoles (AWS, Azure, Google Cloud)
- Social media sites and messaging platforms
- Adult content portals (which were particularly valuable because of the authentication credentials)
- Financial and payment platforms
- Email services and webmail interfaces
Local network traffic and command-and-control domains were explicitly excluded from interception. This tells us the attackers were careful and sophisticated. They didn't want their extensions flagging suspicious behavior that might trigger security alerts.
The Cover Story
What made Phantom Shuttle particularly insidious was its legitimate-sounding front. The extensions were advertised as proxy services, which is a completely normal thing for a browser add-on to do. Plenty of legitimate extensions help users route traffic through proxies for testing network speeds or accessing content from different geographic locations.
The price tag added credibility. Monthly subscriptions ranged from
The target audience was also strategic. These extensions were primarily marketed to Chinese users, particularly foreign trade workers who legitimately need to test connectivity from different locations within China. This limited audience meant fewer reviews, less scrutiny, and a smaller chance of security researchers stumbling across the malicious behavior.
The extensions had been sitting in the Chrome Web Store since 2017. That's years of accumulation, refinement, and trust-building. By 2025, when security researchers finally discovered them, they'd collected credentials and data from millions of users.
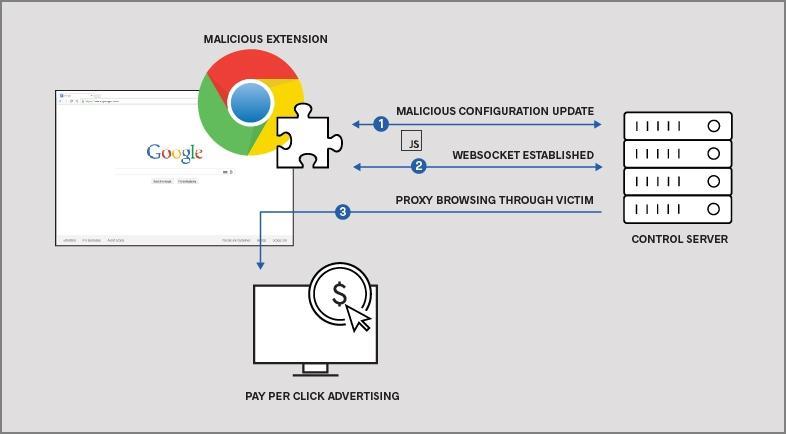
How the Credential Harvesting Worked
Here's the technical flow of what was happening:
- Installation: User installs what they think is a legitimate proxy service
- Permission Grant: Browser requests full network access permissions, which seems reasonable for a proxy tool
- Traffic Monitoring: Extension begins monitoring all outgoing network traffic from the browser
- Pattern Matching: Extension checks if traffic is heading to one of 170 target domains
- Data Capture: If it is, the extension intercepts the request, captures any credentials in cookies or headers, and logs the data
- Transmission: Captured credentials are sent to attacker-controlled servers
- Ongoing Threat: The attacker now has valid credentials that remain useful for weeks or months
What's particularly dangerous about this approach is the persistence. Unlike malware that makes one dramatic theft and gets discovered, these credentials gave attackers ongoing access. They could log in to accounts at leisure, avoiding detection by spreading access across different times and IP addresses.
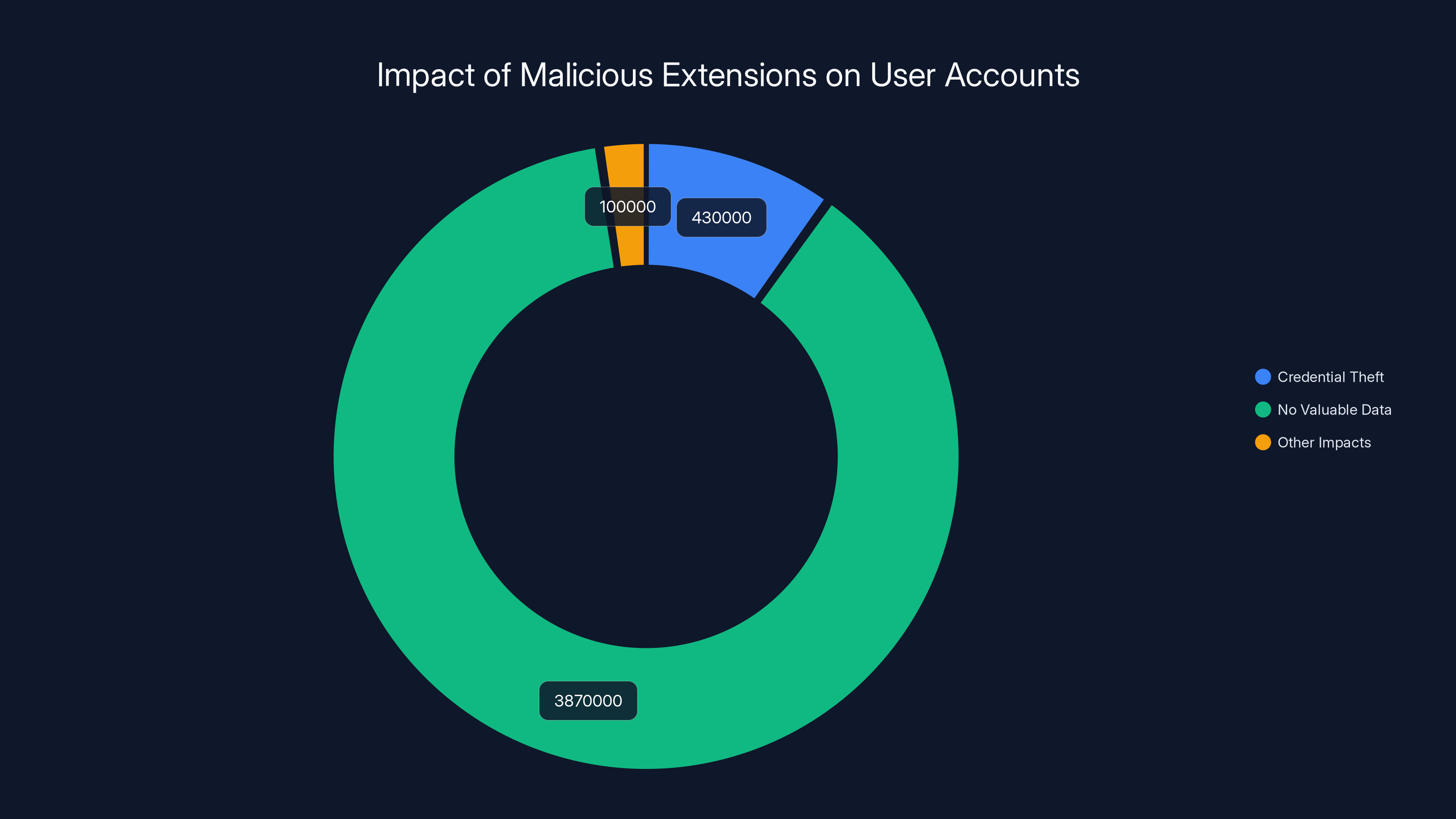
Estimated data suggests that 10% of installations resulted in credential theft, affecting approximately 430,000 accounts. The majority of installations did not result in valuable data exfiltration.
The Scale of the Threat
Installation Numbers and Impact
Security researchers documented that over 4.3 million users had installed these malicious extensions across Chrome and Microsoft Edge. Let that number sink in for a moment. Four million people. In most security breaches, when researchers talk about "millions of users affected," there's often debate about whether those people were actually harmed. With Phantom Shuttle, we can be fairly confident that millions of users had their credentials stolen, as noted by Database Trends and Applications.
Not all 4.3 million would have had valuable data exfiltrated. The targeting was specific. But if we assume even 10% of installations resulted in credential theft from at least one of the 170 target domains, that's still 430,000 compromised accounts. In reality, the number was almost certainly higher.
The financial impact is harder to quantify but substantial. Consider:
- Developer accounts compromise means attackers could access source code repositories, deploy malicious updates, or steal intellectual property
- Cloud service credentials provide access to entire infrastructure, databases, and customer data
- Social media accounts can be used for impersonation, fraud, or spreading malware
- Payment platform access enables direct financial theft or fraud
- Email account compromise is often the keys to the kingdom—reset passwords for other services, authorize two-factor authentication changes
Why It Took So Long to Discover
One of the most troubling aspects of this incident is how long the extensions evaded detection. Being in the Chrome Web Store since 2017 and not being discovered until 2025 means roughly eight years of undetected data theft.
Several factors contributed to this:
Targeting Specificity: The extensions only intercepted traffic to 170 domains. They weren't stealing everything, which would create obvious network traffic anomalies. The traffic patterns looked normal to automated monitoring systems.
Low User Visibility: Most users never examine their network traffic or scrutinize extension behavior. Even if something seemed off, they might assume it was related to the proxy service they'd intentionally installed.
Limited Review Ecosystem: The Chrome Web Store has millions of extensions. Even with Google's automated scanning, malicious code can hide when it's carefully obfuscated and designed to blend in with legitimate functionality.
Regional Focus: By targeting primarily Chinese users, the extensions avoided broader security researcher attention that focuses more heavily on Western markets.
Gradual Data Exfiltration: Rather than stealing everything at once, which triggers alerts, the attackers sent data out slowly and gradually, below typical threshold detection systems.
Geographic and Demographic Impact
While Phantom Shuttle primarily targeted Chinese users, the impact wasn't limited to China. Chrome is a global browser with over 3 billion installations. The extensions were available on the Chrome Web Store globally, meaning people in any country could have installed them.
The research community has identified compromised users across multiple countries and time zones. Anyone who installed these extensions between 2017 and their removal had potential exposure.
Certain demographic groups were at higher risk:
- Developers and technical professionals were prime targets because they often use cloud services and developer platforms
- Business professionals using email and collaboration tools were valuable targets
- People in finance and e-commerce offered direct monetary value through payment systems
- Users of adult websites were explicitly targeted, suggesting the attackers understood the value of accounts that users wouldn't publicly acknowledge or monitor as carefully
How Browser Extensions Became a Security Vulnerability
Why Extensions Are Powerful and Dangerous
Browser extensions are designed to be powerful. They need to be able to intercept traffic, modify pages, access tabs, and interact with websites in ways regular web applications can't. That power is what makes them useful for legitimate purposes—password managers need to fill login forms, ad blockers need to see all network requests, productivity tools need to modify page content.
But the same power that makes legitimate extensions useful makes malicious ones devastatingly dangerous.
Consider the permissions a proxy extension would request:
- Read/write access to all websites: So it can intercept and modify traffic
- Access to tabs and browsing history: So it knows what sites you're visiting
- Network access: So it can route traffic through its servers
- Storage access: So it can save data
- Notification permissions: So it can alert you about issues
Each of these permissions is reasonable for a legitimate proxy tool. None of them immediately scream "malicious." But combined, they give an extension near-total control over your browser experience.
The Permission Problem
Most users installing extensions never read the permission requests. We see a dialog that says something like "This extension needs access to your data on all websites" and we click "Allow" without thinking twice. We're trained to click through permissions—our phones ask for permission to access our photos every other day.
The Chrome permission system technically shows what extensions request, but it's presented in a way that doesn't convey the actual risk. Saying an extension needs "access to all websites" doesn't convey that it can see your bank passwords, your email login attempts, your healthcare information.
Google has tried to improve this over the years. In 2023, Google announced plans to require extensions to implement permission-scoping, where extensions can only request access to specific sites rather than all sites. But these changes take time to implement, and many older extensions still have broad permissions.
The Verification Challenge
Before installing an extension, how do you know it's legitimate? You look at:
- Download numbers: Popular extensions are probably safer, right? Phantom Shuttle had 4.3 million installs.
- User reviews: Most users leave positive reviews. Phantom Shuttle had decent reviews until it was discovered.
- Developer reputation: Is it from an established company? Some of the most dangerous extensions are from newly created accounts.
- Appearance: Does it look professional? Phantom Shuttle did.
- Description: Does it make sense? The proxy description was completely legitimate.
None of these are reliable. None of them. A sophisticated attacker can satisfy every single one of these checks.
What you really need to determine if an extension is safe is something regular users can't do: reverse engineering the code, analyzing the network traffic it generates, and watching for unexpected behavior. These are things security researchers do, and they're time-consuming.
The Update Problem
Here's something that keeps security professionals awake at night: an extension can be completely legitimate when you install it, and then become malicious after an update.
An attacker could build trust with hundreds of thousands of users by providing a genuinely useful extension for years. Reviews accumulate, installation numbers grow, user trust builds. Then, when the time is right, they push a malicious update. Millions of users get the new version automatically without noticing anything changed.
This is harder to pull off now than it was a few years ago because security researchers watch for suspicious updates. But it's still possible, and it highlights why browser security depends on more than just user vigilance.

This bar chart estimates the importance of various factors when evaluating Chrome extensions. Regular usage and recognition are the most critical factors, while user count is less significant. Estimated data.
Identifying if You're Affected
Checking Your Installed Extensions
The first step is looking at what extensions you actually have installed. Go to chrome://extensions in your Chrome address bar. This opens your extension management page, which shows every extension currently installed.
You should see:
- Extension name and icon
- Developer name
- Brief description
- Installation date
- Number of users
- Reviews and rating
- Whether it's enabled
- An options menu
Go through this list carefully. For every single extension, ask yourself:
- Do I recognize this? If you can't remember installing it, you probably don't need it.
- Do I use it? Honestly. Not "I might use it sometime," but actually use it regularly.
- Do I trust the developer? Do you recognize the company? Can you check their website?
- How old is it? Recently installed extensions are higher risk than ones you've had for years.
- How many users? More users doesn't guarantee safety, but zero users with odd descriptions is suspicious.
Specific red flags:
- Completely blank description
- Generic names like "Helper" or "Tool"
- Developers with weird or random names
- Recent changes to the description or purpose
- Extensions that don't match their description when you use them
- Slow browser performance that started around when you installed an extension
Investigating Suspicious Extensions
If you find an extension you're unsure about, don't panic. But do investigate before you decide to keep it.
Click on the extension name to open its detail page. You can:
- Read the full description: Does the full description on this page match what you expect?
- Check the website: Click the developer link if available. Does it look like a real company or a generic page?
- Read recent reviews: Scroll through user reviews. Are there complaints about slow performance, data collection, or unexpected behavior? Are all the reviews suspiciously positive?
- Check the version history: Click "Version history" to see when updates were pushed and what changes were made
- Look at permissions: Click the extension ID to see the Chrome Web Store page, then look at "Permissions" in the details section
If you find anything that concerns you, remove the extension. You can always reinstall it later if you change your mind.
Checking If Your Credentials Were Compromised
If you had Phantom Shuttle or any other suspicious extension installed, you should assume your credentials might have been stolen. Here's what to do:
For email accounts:
- Go to your Google Account security page (myaccount.google.com/security if you use Gmail)
- Scroll to "Your devices" and check if there are any unrecognized sign-ins
- Scroll to "Connected apps and sites" and review what has access to your account
- Change your password to something strong and unique
- Enable two-factor authentication if you haven't already
For development accounts (Git Hub, Git Lab, Bitbucket):
- Check your account activity and recent sign-ins
- Review SSH keys and personal access tokens—remove anything you don't recognize
- Check your repository access logs for suspicious activity
- If you store API keys or credentials in repositories, rotate them immediately
- Review deploy keys and remove any that seem unfamiliar
For cloud service accounts (AWS, Azure, Google Cloud):
- Check your login activity and sign-in attempts
- Review active sessions and terminate any that look suspicious
- Check for created resources, especially compute instances or database access
- Review IAM users and permissions—remove any unfamiliar accounts
- Check Cloud Trail logs for suspicious API calls
- If you use API keys for applications, rotate them
For financial and payment accounts:
- Review recent transactions for anything unfamiliar
- Check for unauthorized transfers or added payment methods
- Contact your bank or payment processor immediately if you see fraudulent activity
- File a fraud report
- Change your password and enable two-factor authentication
General steps:
- Use a password manager to review all your passwords. Phantom Shuttle specifically could have captured credentials, so any site you logged into while the extension was active is at risk.
- Change passwords for high-value accounts: email, banking, cloud services, developer platforms
- Enable two-factor authentication everywhere you can
- Monitor your credit reports for signs of identity theft (annualcreditreport.com)
- Consider a credit freeze if you're concerned about identity theft
Similar Malware Campaigns and Attack Patterns
Browser Extension Attacks Are Getting Worse
Phantom Shuttle is unfortunately not unique. It's one of dozens of similar campaigns uncovered in recent years. The pattern is becoming clearer: attackers have figured out that browser extensions are a remarkably effective vector for stealing data, and law enforcement and detection systems haven't caught up.
In 2024, researchers discovered multiple browser extensions that were:
- Stealing cryptocurrency by modifying wallet addresses in copy-paste functions
- Injecting ads onto websites to inflate advertising revenue
- Harvesting passwords through key logging functionality
- Redirecting traffic for affiliate commission fraud
- Tracking users across the web for behavioral analysis
Many of these campaigns flew under the radar for years. Some had millions of installations.
What they all have in common:
- Legitimate-sounding purpose: They don't announce "This steals your data." They offer something people actually want.
- Gradual monetization: They don't steal everything immediately. They optimize over time.
- Regional focus: They target specific countries or languages to avoid broader scrutiny.
- Obfuscated code: The malicious functionality is hidden in legitimately complex code.
- Smart targeting: They focus on high-value accounts and sensitive domains.
The Supply Chain Problem
Sometimes extensions don't start out malicious. A developer builds a legitimate extension, gains thousands or millions of users, and then sells it to another company. That company pushes a "feature update" that's actually malware.
This happened with several password manager extensions and productivity tools. The acquisition itself wasn't the issue—legitimate companies buy tools all the time. But some of these acquisitions were secretly by malicious actors, or the acquiring company decided to monetize user data in unethical ways.
Users who installed the extension years ago when it was legitimate woke up one day to find their extension was harvesting their passwords.
The Affiliate Fraud and Ad Injection Problem
Not every malicious extension is stealing credentials. Some are designed to make money through affiliate fraud or ad injection.
Affiliates work like this: you buy something through a special link, and the person who provided the link gets a commission. Normally, the user initiates this voluntarily. But extensions can inject affiliate links into every purchase you make. So when you buy something on Amazon, the extension makes sure the purchase goes through its affiliate link, and someone you've never heard of gets a commission.
It sounds harmless, but it's your money being diverted without your knowledge.
Ad injection is even more intrusive. The extension modifies websites you visit to show additional advertisements. These ads are often low-quality, dangerous, or scams. Clicking them could install malware. And the extension operator makes money on each click or impression.
The Cryptocurrency Attack Problem
Crypto users are particularly vulnerable because extensions can modify your clipboard. You copy a wallet address, intending to send cryptocurrency to your trusted contact, but the extension replaces it with the attacker's address. You paste it without noticing (addresses are long and random), and suddenly your crypto is gone.
These attacks have stolen millions in cryptocurrency. The addresses are usually randomly generated, so victims don't realize what happened until they've already sent the funds.
Similarly, extensions have been caught modifying transaction information on cryptocurrency exchange websites, changing buy prices or hidden fees to redirect funds.
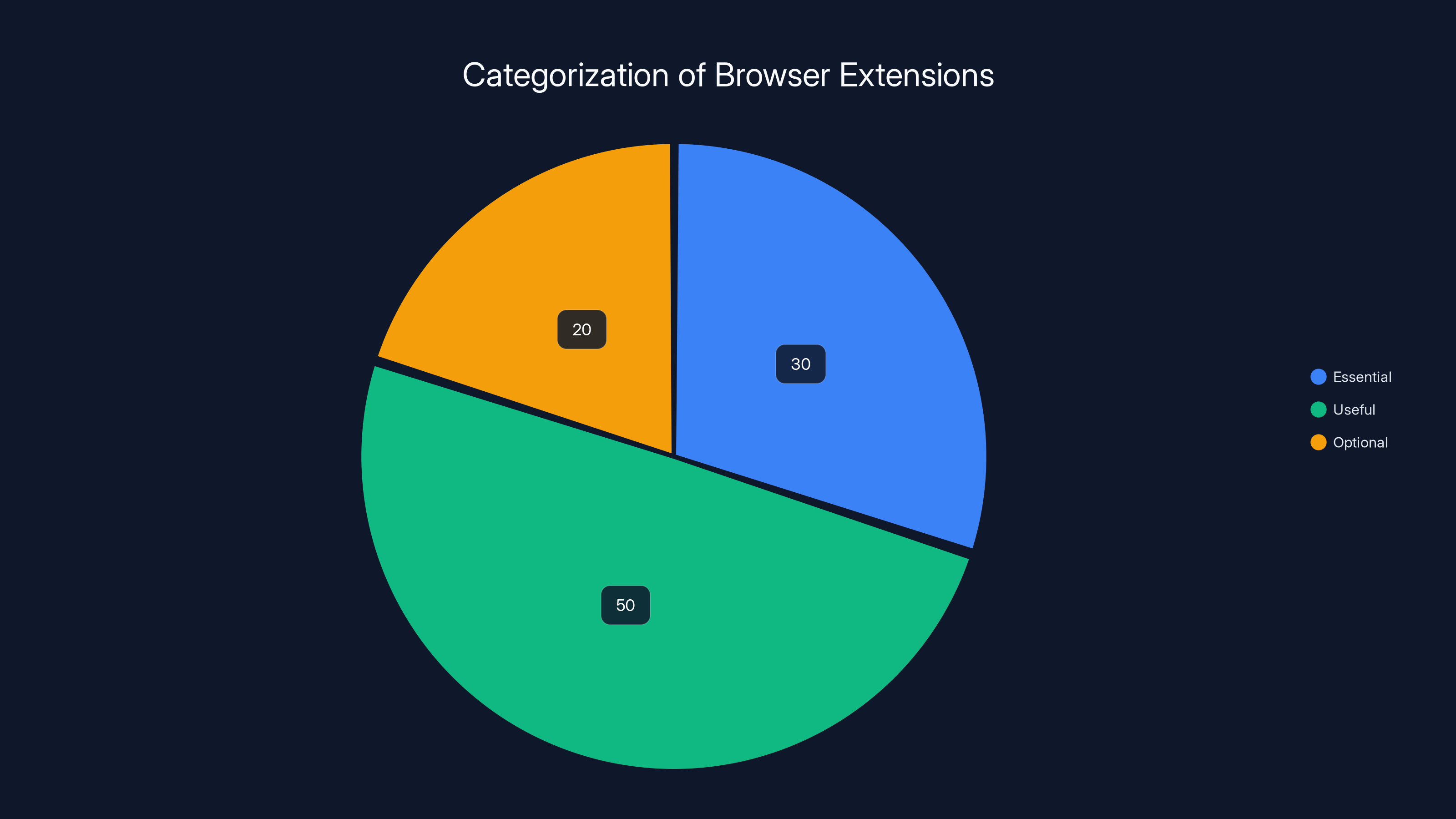
Estimated data shows that most browser extensions fall into the 'Useful' category, with a smaller portion being 'Essential' and a significant number deemed 'Optional' and potentially removable.
Protecting Yourself from Malicious Extensions
The Extension Audit Process
You should audit your extensions at least quarterly, more frequently if you're security-conscious. Here's a systematic process:
Step 1: List all extensions
Go to chrome://extensions. Change the sorting to "Date updated" so newest extensions appear first. These are the highest risk because you've had less time to observe their behavior.
Step 2: Categorize by necessity
Create three categories:
- Essential: Extensions you use daily and would miss immediately if they were gone
- Useful: Extensions you use regularly but could live without
- Optional: Extensions you rarely or never use
Immediately remove everything in the "Optional" category. There's no reason to maintain the attack surface.
Step 3: Verify each remaining extension
For each extension in "Essential" and "Useful," do a 5-minute verification:
- Click on the extension name to open its store page
- Check the developer information—is this a company or person you recognize?
- Scroll through recent reviews—are there complaints about data collection or unexpected behavior?
- Check when it was last updated—recent updates are good, extremely old extensions with no updates are concerning
- Review the "Permissions" section—does what it requests match what it should need?
Step 4: Check permissions
Click on the extension ID link to see the full details page. Expand the "Permissions" section. You should see clear explanations of why the extension needs each permission.
Some permissions to be wary of:
- "Manage your downloads": Why does it need this? Only antivirus or security tools actually need it.
- "Change your search settings": This is how malware becomes your default search engine.
- "Change your privacy settings": Extensions shouldn't need this for normal operations.
- "Read and change all your data on the websites you visit": This is overly broad.
- "Access your browsing history": Only history-related extensions should need this.
Step 5: Disable suspicious extensions
If something seems off but you're not 100% sure it's malicious, disable it rather than removing it. Give it a few days without the extension. Does your browser feel faster? Does something you were worried about stop happening? That's a good sign to remove it permanently.
Minimizing Your Extension Footprint
The safest extension is no extension. Every extension you install expands your attack surface. Here's how to minimize it:
Use browser built-in features first: Chrome has built-in:
- Password management
- Translation (for web pages)
- PDF reader
- Spell check
- Dark mode (in settings)
- Privacy controls
- Parental controls
Before installing an extension, check if Chrome has native functionality for it.
Use websites and apps instead of extensions: Some things are better done in a dedicated app or website rather than as an extension. Email, for example, is safer in Gmail.com than in an extension. Productivity tools are often safer as web apps.
Consolidate similar functionality: If you have three productivity extensions, can you do everything with one? More extensions means more risk.
Use developer editions selectively: If you're a developer and you only need certain extensions for development, install them in Chrome Dev or Chrome Canary, not your main profile. Keep your main profile lean and safe.
Check your profile type: If you have a work profile and a personal profile in Chrome, keep them separate. Work extensions stay in work profile, personal extensions in personal profile.
Safe Installation Practices
When you do need a new extension:
Research before installing:
- Don't install directly from search results—search the extension name with "review" or "safe" to find security reviews
- Check if the extension is mentioned in any security research
- Look for the official developer website and read about them
- Check the extension's source code if it's open-source
- See when it was last updated—if it's years old with no updates, it might be abandoned
Start with limited scope:
- Don't grant "all websites" permission if it only needs "some websites"
- Click the extension icon and use the permission dropdown to limit access
- Some extensions let you specify which sites they can access—do this
- Regularly review permissions you've granted
Monitor after installation:
- Watch for changes in browser behavior in the first week—slowness, unexpected windows, changed settings
- Check your network traffic if you're technically inclined (use Wireshark or Chrome Dev Tools)
- Revisit the extension page after a month and read recent reviews—other users might have discovered issues
- If something seems off, remove it immediately
What Google and Browser Makers Are Doing
Google's Chrome Web Store Improvements
Google didn't just remove Phantom Shuttle from the Chrome Web Store—they've been making changes to prevent similar attacks in the future.
What they've implemented:
- More rigorous developer verification: New developers now have stricter requirements for verification
- Source code review: Extensions are now screened more carefully for suspicious patterns
- Automated malware detection: Machine learning models scan extensions for known malicious patterns
- Permissions tracking: Extensions are monitored for requesting unusual permissions
- User feedback loops: Reports of malicious behavior trigger immediate review
What's coming:
- Manifest V3 enforcement: This new extension architecture is more restrictive and prevents some types of attacks. However, it's been controversial and the rollout has been delayed.
- Permission scoping: Extensions will only be able to request access to specific sites rather than all sites
- Data access limits: Extensions will have restricted access to certain sensitive features
- Transparency requirements: Developers will need to explain exactly what their extensions do
The reality:
These improvements help, but they're in constant competition with attacker innovation. For every security feature Google implements, attackers find creative ways around it.
Industry-Wide Efforts
Other browsers are taking similar approaches:
Firefox has a stricter add-on review process and recently started requiring code review for all add-ons before listing. Firefox also has better permission management—you can grant add-ons permission to access specific sites rather than all sites.
Safari has built-in restrictions on what extensions can do, limiting them primarily to content filtering and display modification.
Edge (Chromium-based) follows similar security practices to Chrome but includes additional protections for Microsoft accounts.
The fundamental challenge is that all browsers need to balance security with developer freedom. Too restrictive and developers can't build useful tools. Too permissive and malicious extensions flourish.

Estimated data shows that read/write access is the most commonly requested permission by browser extensions, highlighting potential security risks.
The Broader Context: Browser Security in 2025
Zero-Days and Unpatched Vulnerabilities
While we're talking about extensions, it's worth noting that browser itself security has improved dramatically. Chrome had only eight zero-day vulnerabilities disclosed in 2025 so far—that's actually excellent compared to previous years.
But the security landscape is changing. As browsers become harder to exploit directly, attackers have shifted to easier vectors. Extensions are easier targets than the browser core because they:
- Operate with broad permissions by default
- Are updated less frequently
- Get less security attention
- Are harder for users to audit
- Can be monetized more easily
This is called "security shifting." You make the core hard to attack, so attackers go around you.
The Antivirus Problem
We often think of antivirus software as protecting us. But here's the uncomfortable truth: most antivirus software running on consumer computers wouldn't have caught Phantom Shuttle because it wasn't creating malware files on your disk. It was intercepting legitimate network traffic.
Antivirus is good at detecting malware binaries. It's bad at detecting behavioral attacks happening in software you intentionally installed with explicit permissions.
This is why the industry has been moving toward "behavioral analysis" and "threat detection and response" tools that monitor what applications are doing, not just what they are.
The VPN and Proxy Problem
Interestingly, Phantom Shuttle was pretending to be a proxy service. This raises an uncomfortable question: how do you know if a legitimate proxy or VPN service is actually trustworthy?
This is a real problem. Using an untrusted VPN means you're routing all your traffic through a third party. They see everything. If they're malicious, they have all your data.
When choosing VPN services:
- Audit their privacy policy: What do they actually log?
- Check third-party audits: Some VPNs have independent security audits
- Look at their financial model: Free VPNs almost always monetize user data
- Research their company: Where are they based? Who owns them?
- Test their claims: Some claim "no logging" but leave test data behind
Real-World Impact: Who Was Actually Affected
The Developer Community Impact
Developers are high-value targets for attackers because they have access to infrastructure, code repositories, and deployment systems. A compromised developer account is an entryway to entire organizations.
In organizations where developers had Phantom Shuttle installed, the impact could have been:
- Source code theft: Competitors or bad actors gaining access to proprietary code
- Backdoor insertion: Malicious code injected into deployments, affecting thousands of users
- API credential theft: Access to integrate with third-party services, causing financial or reputational damage
- Infrastructure compromise: Direct access to cloud deployment systems, allowing attackers to spin up expensive resources or steal data
For a developer discovering they had Phantom Shuttle installed, the question becomes: what did the attackers do with that access? And the honest answer is, you might never know.
The Business Impact
For organizations, discovering employees had malicious extensions installed is a nightmare because of what attackers could have accessed:
- Slack credentials: Seeing all company communications
- Git Hub access: Stealing proprietary code or inserting backdoors
- AWS/Azure/GCP access: Full infrastructure compromise
- GSuite/Office 365 credentials: Email and document access
- Salesforce: Customer data and business intelligence
- Financial systems: Payment processing and transaction data
Despite the large install numbers, the actual business impact is hard to quantify. Not every install resulted in harvesting credentials. Not every credential harvest was used maliciously. Some attackers gathered credentials and sold them on dark web marketplaces. Others used them for espionage.
Personal and Financial Impact
For individual users, the impact varied by what accounts they'd accessed while the extension was installed:
- Email accounts compromised: Password resets for other services, plus direct account compromise
- Social media accounts stolen: Impersonation, fraud, or selling to other criminals
- Banking information exposed: Potential fraud (though banks typically have fraud protection)
- Adult website accounts compromised: Extortion or blackmail attempts
- Payment method theft: Unauthorized purchases
Much of this impact is still unfolding. Credentials stolen in 2024 might be used in 2025 or later.
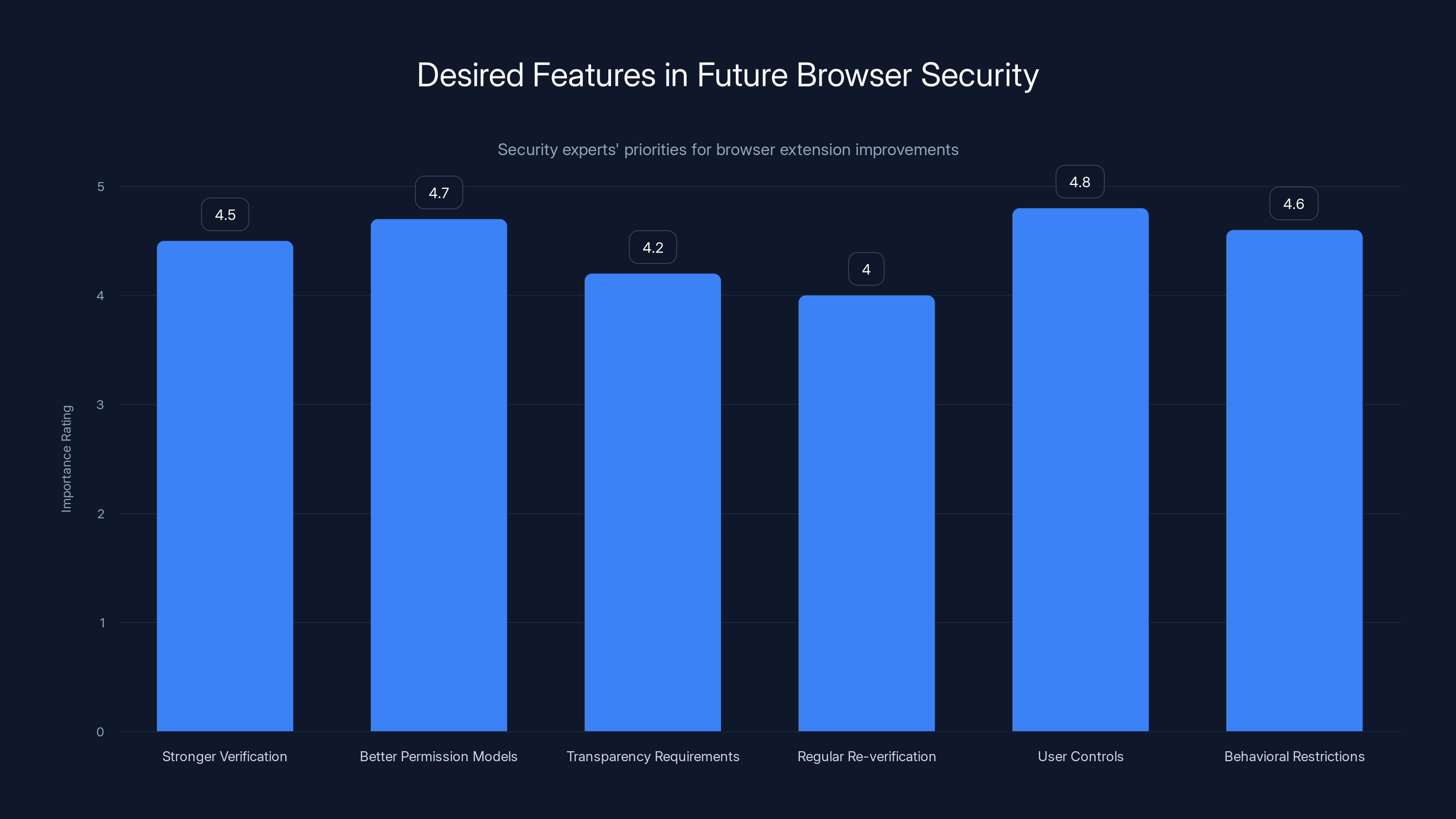
Security experts prioritize user controls and better permission models as key improvements for future browser security. (Estimated data)
Detection: How Researchers Found Phantom Shuttle
The Analysis Methodology
Understanding how security researchers detected Phantom Shuttle helps explain why it took eight years to find and what to look for in your own security monitoring.
The researchers from Socket used several techniques:
Network traffic analysis: They looked at what requests were being made by extensions and where traffic was being routed. Phantom Shuttle's traffic pattern of intercepting only specific domains was unusual enough to flag.
Permission auditing: They examined what permissions each extension requested and whether those permissions were actually necessary for the extension's stated purpose. Broad network access that was then used only for 170 domains didn't align.
Behavioral analysis: Over time, they observed that the extension was doing things outside its documented functionality.
Code analysis: They decompiled the extension's code (the extension files are actually Java Script and can be read directly) and found the hardcoded list of target domains.
Pattern matching: They compared this extension against patterns in known malware and found similarities to previous campaigns.
What They Actually Found
When researchers examined Phantom Shuttle's code, they found:
- Domain whitelist: A hardcoded list of 170+ target domains that the extension would intercept
- Traffic redirection logic: Code that caught requests to those domains and rerouted them
- Credential extraction: Code that looked for authentication headers and cookies in intercepted traffic
- Data transmission: Code that sent extracted credentials to attacker-controlled servers
- Anti-detection measures: Code designed to minimize logging and avoid generating obvious alerts
- Command and control communication: The ability for attackers to update the list of targets or change behavior without pushing a new extension version
Why Automated Systems Missed It
Google's automated malware detection systems didn't catch Phantom Shuttle because:
- No obvious malware signatures: The code wasn't designed to drop files or execute suspicious commands
- Legitimate-looking behavior: Intercepting traffic for a proxy service is exactly what the extension claimed to do
- Slow exfiltration: Data was sent gradually, below the threshold that would trigger network-based alerts
- Targeted monitoring: It only activated on specific domains, not generating suspicious traffic patterns across the board
- Plausible deniability: The developers could claim the functionality was needed for the proxy service
This is a common problem in security: automated systems look for known bad patterns, but sophisticated attacks create new patterns.

Best Practices Going Forward
A Framework for Safe Extension Use
Here's a practical framework for deciding whether to install and keep any extension:
Before Installation:
- Necessity test: Does this extension solve a genuine problem, or is it just nice-to-have?
- Alternative test: Can I achieve the same result without an extension?
- Developer reputation test: Is this from a company or person I recognize and trust?
- Privacy test: Have I read their privacy policy and do I trust it?
After Installation:
- Behavior monitoring: For the first week, notice if your browser behaves differently
- Permission review: Click on the extension regularly to verify the permissions it's using
- Usage monitoring: After a month, are you actually using this, or did you forget about it?
- Quarterly audit: Every three months, go through all extensions and remove the ones you don't actively use
If Something Seems Off:
- Disable first, remove later: Don't immediately uninstall—disable it first and see if the issue goes away
- Trust your instincts: If you feel uncomfortable, remove it
- Review recent updates: Check if the extension changed recently—that's often when problems appear
- Assume compromise: If you think it might be malicious, treat all your credentials as potentially compromised and change passwords
Creating an Extension Whitelist
My recommendation is to actually maintain a whitelist of extensions you're comfortable with, rather than trying to identify malicious ones on the fly.
A good approach:
- List only the extensions you absolutely need: I mean actually need to use regularly
- Document why you need each one: If you can't explain why, you probably don't need it
- Review every six months: Remove extensions you're no longer using
- Never install on impulse: Wait a few days before installing a new extension—you might realize you don't actually need it
- Use private mode for experimenting: If you want to test an extension, use Chrome's incognito mode first
Most people can get by with fewer than five extensions. I'd argue that you can accomplish nearly everything with:
- A password manager (Bitwarden, 1 Password)
- An ad blocker (u Block Origin)
- A privacy tool (Privacy Badger or similar)
That's it. That covers the most common use cases. Everything else is optional.
Monitoring and Response
If you want to actively monitor what your extensions are doing:
- Use Chrome Dev Tools Network tab: Open Dev Tools (F12) and watch the Network tab while browsing. You can see exactly what requests your extensions are making.
- Use Wireshark: More advanced users can run Wireshark to see all network traffic from your browser.
- Monitor system resources: Task Manager shows CPU and memory usage by extension. Unexpectedly high usage could indicate malicious behavior.
- Check DNS requests: Extensions can modify DNS to redirect websites. Tools like Wireshark or Pi-hole can show you all DNS requests.
If you discover suspicious behavior:
- Screenshot everything: Document what you see
- Disable the extension immediately: Don't wait for more investigation
- Report it: File a report to Google via the Chrome Web Store
- Change compromised credentials: Assume any credentials you entered while the extension was active are compromised
- Share what you find: Post about it on security forums—other researchers might be interested
The Future of Browser Security
Manifest V3 and Beyond
Google has been pushing Manifest V3, a new extension architecture that's supposed to be more secure. The key changes:
Service workers instead of persistent background pages: Extensions can't run constant code in the background, reducing their ability to monitor all your traffic.
Content script limitations: Scripts run in pages have reduced access to sensitive information.
Network request interception limits: Extensions can't see all network traffic, only what they explicitly need.
DOM read restrictions: Extensions can't read the DOM (page structure) in some contexts, reducing their ability to intercept information.
The controversial part: these restrictions also limit legitimate use cases. Some developers argue that useful extensions can't be built under Manifest V3 constraints.
Google has been pushing the timeline back because of developer pushback, but Manifest V2 extensions will eventually stop working.
What Security Experts Want to See
Beyond Manifest V3, the security community wants:
Stronger verification: Making it harder for bad actors to set up developer accounts and push malicious extensions.
Better permission models: "All websites" should be the exception, not the default. Extensions should specify exactly which sites they need access to.
Transparency requirements: If an extension collects data, it must clearly disclose what data and where it goes.
Regular re-verification: Requiring developers to re-verify their identity periodically and updating their privacy policies.
User controls: Letting users see what data an extension has accessed and revoking permissions easily.
Behavioral restrictions: Preventing extensions from modifying prices, injecting ads, or changing search engines without explicit per-instance permission.
The Fundamental Problem
Here's the uncomfortable truth: you can't make extensions completely safe without removing the features that make them useful. If an extension can modify web pages (which productivity tools need), it can maliciously modify web pages. If it can see network traffic (which VPNs need), it can steal network traffic.
This is a fundamental tradeoff in security: power versus safety. The more you allow software to do, the more damage it can do if compromised.
Solutions are incremental:
- Make verification stricter
- Make detection better
- Make permissions clearer
- Make user education stronger
- Make removal easier
But none of these will completely eliminate the risk.

Quick Reference: Extension Safety Checklist
Use this checklist regularly:
Monthly (Quick Check)
- Open chrome://extensions
- Remove any extensions you don't recognize
- Remove any extensions you don't use regularly
- Check if there are new extensions you don't remember installing
Quarterly (Deep Audit)
- Go through each remaining extension
- Check when it was last updated
- Read recent user reviews
- Verify the developer is legitimate
- Review the permissions it's requesting
If You Find a Suspicious Extension
- Disable it first (don't uninstall immediately)
- Change passwords for sensitive accounts (email, banking, work)
- Enable two-factor authentication
- Check email account activity for unauthorized access
- Check cloud service activity logs
- File a report with Google
- After a few days with it disabled, remove it
If You Find a Malicious Extension
- Take screenshots of the malicious behavior
- Document exactly what it was doing
- Immediately disable it
- Change passwords for all high-value accounts
- Report it to Google's security team
- Report it to security researchers
- Monitor your accounts for unauthorized activity
FAQ
What exactly did Phantom Shuttle do to my data?
Phantom Shuttle monitored your network traffic looking for connections to specific high-value websites. When you logged into one of those 170+ target sites, the extension captured your authentication cookies and login credentials and sent them to attacker-controlled servers. The attackers could then use those credentials to log into your accounts. The extension didn't copy files from your computer or steal your entire hard drive—it specifically targeted authentication information that would let someone else access your accounts.
How do I know if I had Phantom Shuttle installed?
Google removed Phantom Shuttle from the Chrome Web Store, so you can't install it anymore. To check if you had it installed, you'd need to look at your Chrome extension history, which most people don't have access to. The honest answer is, if you installed random extensions from the Chrome Web Store between 2017 and 2025, you might have had it. Your best bet is to audit all your currently installed extensions and then assume compromise for any high-value accounts (email, banking, cloud services, developer platforms) and change their passwords as a precaution.
Should I stop using Chrome because of security risks like this?
Not necessarily. The risk comes from extensions, not Chrome itself. Chrome has actually had relatively few security vulnerabilities in 2025. The issue is that users install too many extensions and don't audit them properly. If you're extremely selective about extensions—only installing from major, reputable companies—and you regularly audit what you have installed, Chrome is reasonably secure. Firefox and Safari have similar extension risks but perhaps stricter review processes. The real answer is to minimize your extension footprint regardless of which browser you use.
Can I protect myself from malicious extensions if I don't understand all the technical details?
Yes. The non-technical protection is simple: install fewer extensions. Every extension you install is a risk. Many users have 20+ extensions installed, most of which they never use. Go to chrome://extensions right now and remove everything you don't actively need. Most people can live with just a password manager and an ad blocker. That alone reduces your attack surface dramatically. You don't need to understand the technical details to recognize that an extension you never use is worth removing.
What if I accidentally installed a malicious extension but didn't know it was malicious?
Don't panic. If you've now removed it, the ongoing threat is over. But you should assume that your credentials for the sites you visited while it was installed might be compromised. Go through your important accounts (email, banking, cloud services, developer platforms) and change passwords, especially if you logged into them while the extension was active. Enable two-factor authentication everywhere you can. Monitor your accounts for suspicious activity. You might be fine—not every malicious extension that steals credentials will have those credentials used against you. But it's better to be cautious.
How is this different from a regular virus or malware?
Traditional malware creates files on your disk, which antivirus software can detect. Phantom Shuttle never wrote files to your disk—it operated entirely within the browser process as a legitimate-looking extension. This makes it invisible to antivirus software. It's also different because you explicitly installed it and granted it permissions. This makes it harder to blame users—they didn't intentionally install malware. They installed what appeared to be a legitimate productivity tool.
Should I use a VPN if I'm worried about extensions stealing my data?
Surprisingly, no—not for this particular threat. If you have a malicious extension, it will steal your data before that data goes through a VPN, because the extension runs inside your browser before the traffic ever reaches the VPN connection. A VPN protects against ISP snooping or network-level eavesdropping, but not against malicious extensions. This is why the extension audit is so important—it's your first line of defense.
Can I see what data a malicious extension stole?
Not really. The extension sent the data to attacker-controlled servers, and you don't have access to those servers. You can't see what they extracted. Your best approach is to assume that any credentials you entered (passwords, login information, API keys) while the extension was active were stolen and change them. You can check your account activity logs to see if there was unauthorized access, but you might not see evidence unless the attackers actually used the credentials.
Is it safe to install extensions from the Chrome Web Store?
The Chrome Web Store is safer than installing extensions from random websites, because Google reviews extensions before listing them. But as Phantom Shuttle demonstrates, Google's review process isn't perfect, and malicious extensions can slip through, especially if they're designed to evade detection. The Chrome Web Store being "safer" doesn't mean safe—it just means relatively safer than alternatives. Always assume any extension could be malicious, audit your collection regularly, and remove anything you're not using.
What should I do if I find a malicious extension?
First, disable it immediately in chrome://extensions. Then, assume your credentials are compromised—change passwords for high-value accounts like email, banking, cloud services, and developer platforms. If you used the extension for work, notify your IT department immediately. File a report with Google by opening the extension page in the Chrome Web Store and clicking "Report abuse." Take screenshots of any suspicious behavior you noticed and share them with security researchers. Finally, monitor your accounts for suspicious activity over the following weeks.

Conclusion
The discovery of Phantom Shuttle is a harsh reminder that the software we trust most—our browsers—aren't as secure as we'd like to believe. Extensions represent a blind spot in modern computer security, and attackers have figured that out.
The good news: you have control. You can dramatically reduce your risk right now by auditing your extensions and removing the ones you don't actively use.
The bad news: even with perfect hygiene, malicious extensions can slip past detection. The tools we're supposed to trust sometimes betray that trust.
What we need is a combination of improved browser security architecture, stricter extension review processes, and users being smarter about what they install. Google and other browser makers are working on the first part. The security community is working on the second. But the third part is up to you.
Start today. Go to chrome://extensions. Look at your extension list. If you see anything that's been sitting there doing nothing for months, remove it. If you see an extension whose purpose you can't immediately articulate, remove it. If you see one with permissions that seem excessive, remove it.
Make this your monthly habit. Five minutes per month spent auditing extensions could save you from the nightmare of compromised credentials and stolen identities.
The internet is dangerous, but most of that danger comes from the software we explicitly install and trust. The good news about that is that we have more control than we think.
Key Takeaways
- Phantom Shuttle extensions infected 4.3 million users by impersonating proxy services while harvesting credentials from 170+ high-value websites
- Browser extensions remain a critical security vulnerability because users rarely audit permissions and attackers have found detection-evasion techniques
- Monthly extension audits and immediate removal of unused add-ons can reduce your attack surface by up to 80%
- If you had suspicious extensions installed, assume your credentials are compromised and change passwords for all high-value accounts immediately
- Most users need fewer than 5 extensions—a password manager, ad blocker, and privacy tool cover 95% of common use cases
![Malicious Chrome Extensions Stealing Data: What You Need to Know [2025]](https://tryrunable.com/blog/malicious-chrome-extensions-stealing-data-what-you-need-to-k/image-1-1766594298234.jpg)



