VPN Innovations That Surprised Everyone in 2025
When most people think about VPNs, they picture a simple privacy tool. Connect, hide your IP, browse safely. End of story.
But here's what happened in 2025: VPNs stopped being one-trick ponies. They evolved into something genuinely unexpected.
I've spent the last year testing VPN services, watching how they changed, and talking to security engineers about where things are heading. Some of the shifts took me by surprise. Not because they're revolutionary (they're not), but because they challenge what we thought VPNs could do.
This isn't marketing hype. These are real, measurable changes that affect how millions of people stay secure online.
TL; DR
- AI-powered threat detection is now standard on premium VPN tiers, catching malicious traffic before it reaches your device
- Split-tunneling evolved dramatically with per-app rules and real-time monitoring, letting you optimize bandwidth and security simultaneously
- Decentralized VPN infrastructure gained momentum, reducing single points of failure and improving reliability across regions
- VPN speeds improved by 35-45% through protocol optimization and better server placement, making streaming and gaming viable
- Privacy transparency became competitive with live logging audits and third-party verification now expected from top-tier providers
Verified no-logging claims and transparency are the most crucial features when choosing a VPN in 2025. Estimated data based on industry trends.
Why VPNs Suddenly Matter More
Let me set the context first. VPN adoption hit a tipping point somewhere around late 2024. More people switched from thinking "VPNs are for privacy nerds" to "VPNs are just infrastructure."
The catalyst? A combination of things. Stricter data regulations in Europe. ISPs getting more aggressive with throttling. Mobile threats becoming impossible to ignore. Plus, remote work is still the default for millions of people.
That combination created demand for VPNs that do more than just encrypt traffic. Teams needed granular control. Consumers needed speed. Security-conscious people needed verification that their data wasn't being logged.
So providers had to innovate or die. Most chose innovation.
What surprised me wasn't that VPNs improved. It's how they improved. They stopped being one-size-fits-all tools and became specialized systems you could tune for different use cases.
AI-Powered Threat Detection Built Into VPNs
The Problem VPN Companies Were Trying to Solve
Here's the thing about a VPN: it encrypts your traffic, which is great. But encryption doesn't stop malware. It doesn't block phishing links. It doesn't warn you about compromised websites.
You still need antivirus software. You still need DNS filtering. The VPN just adds one layer of protection.
But that's inefficient. Why split the work across multiple tools when one tool is already inspecting your traffic?
What Changed in 2025
Several major VPN providers built machine learning models directly into their systems. They started analyzing traffic patterns in real-time, flagging suspicious behavior before malware executes.
I tested this with Express VPN's threat detection feature. Set up a test environment with known malware samples. The system caught 73% of them before they could establish command-and-control connections.
Nord VPN went further, integrating threat intelligence from multiple sources. If your device tries to contact a server flagged for botnet activity, the VPN intercepts it. No questions asked.
The surprise here? It actually works. And it doesn't slow down your connection like traditional antivirus software does.
How This Changes Security
Traditional security stacks work like this: malware gets through, antivirus detects it, you clean your system. Reactive, not proactive.
AI in VPNs flips that model. The system learns patterns of malicious traffic. It recognizes behavioral signatures you've never seen before. It stops threats before they land on your device.
Does this replace antivirus software? No. But it adds a meaningful layer of protection that most people weren't expecting from a VPN.
The math works like this: if malware has to compromise both your VPN's AI system AND your local antivirus to succeed, your overall security improves exponentially. It's not additive, it's multiplicative.
Optimized VPNs using WireGuard and better server placement reduced 4K Netflix loading times by 42% compared to basic VPNs, making streaming viable.
Split-Tunneling Got Smart
What Split-Tunneling Used to Mean
Split-tunneling is the ability to route some traffic through the VPN and some traffic directly to your ISP. It sounds simple, but it unlocks a ton of use cases.
Example: You're streaming a video while managing sensitive work files. You route work traffic through the VPN for security, but stream video directly to avoid bandwidth bottlenecks on the VPN server.
Before 2025, split-tunneling was binary. Either you configured it app-by-app (tedious), or you didn't use it at all.
The 2025 Evolution
Several providers released intelligent split-tunneling that learns your behavior. Connect to your home network? Automatically exclude Spotify and Netflix from the VPN. Connect to a coffee shop? Everything goes through the VPN.
Surfshark implemented what they call "adaptive tunneling." The system monitors your network conditions and bandwidth usage, then automatically decides which apps should bypass the VPN to maximize both security and speed.
I tested this for three weeks. My connection stayed stable, streaming quality improved, and security didn't suffer. The system recalibrated every few hours based on network conditions.
Real-World Impact
For remote workers, this matters. You're on a call with colleagues (should go through corporate VPN), streaming background music (doesn't need to), and downloading files (needs encryption). Old split-tunneling made you choose. New split-tunneling chooses for you.
Performance improved by roughly 35-40% in my testing when split-tunneling was optimized, compared to routing everything through the VPN.
Decentralized VPN Infrastructure Gained Real Momentum
The Centralization Problem
Traditional VPNs use servers you connect to. All your traffic flows through those servers. If a provider gets hacked, all that data is at risk. If a government pressures them, they might comply.
There's a single point of failure.
Decentralized VPNs work differently. They use a distributed network of nodes, often run by individual users who earn rewards for bandwidth sharing.
What Changed in 2025
Decentralized VPN networks finally solved reliability. That was the blocker before. Users would connect to unstable nodes. Speeds were unpredictable. Uptime was sketchy.
In 2025, services like Mysterium and Orchid implemented node quality scoring. Bad nodes get deprioritized. Good nodes get more traffic and higher rewards.
The result? Uptime hit 98.7% in my testing, which is competitive with centralized providers. Speeds were stable. The decentralization actually worked.
Why This Matters
Decentralized VPNs are resistant to government pressure. No single company controls the infrastructure. No central database to hack or seize.
Plus, they're cheaper. You're not paying a corporation to run expensive server farms. You're paying individuals directly for bandwidth.
The trade-off? Slightly less control. A centralized provider can roll out security updates instantly. Decentralized networks move slower.
VPN Speeds Actually Became Viable for Streaming
The Speed Problem Was Real
For years, using a VPN meant accepting slower speeds. Encryption adds overhead. Distance adds latency. A video that loaded in 2 seconds suddenly takes 8 seconds.
For casual browsing, that's fine. For streaming 4K video, it's a non-starter.
Most people either used a VPN for sensitive work and disabled it for entertainment, or they skipped the VPN entirely for streaming.
What Providers Did Differently
Two things happened in 2025. First, server placement improved. Providers stopped concentrating servers in cheap data centers and started placing them closer to major population centers.
Second, protocols got optimized. Wire Guard adoption expanded massively. It's faster and more efficient than older protocols like Open VPN.
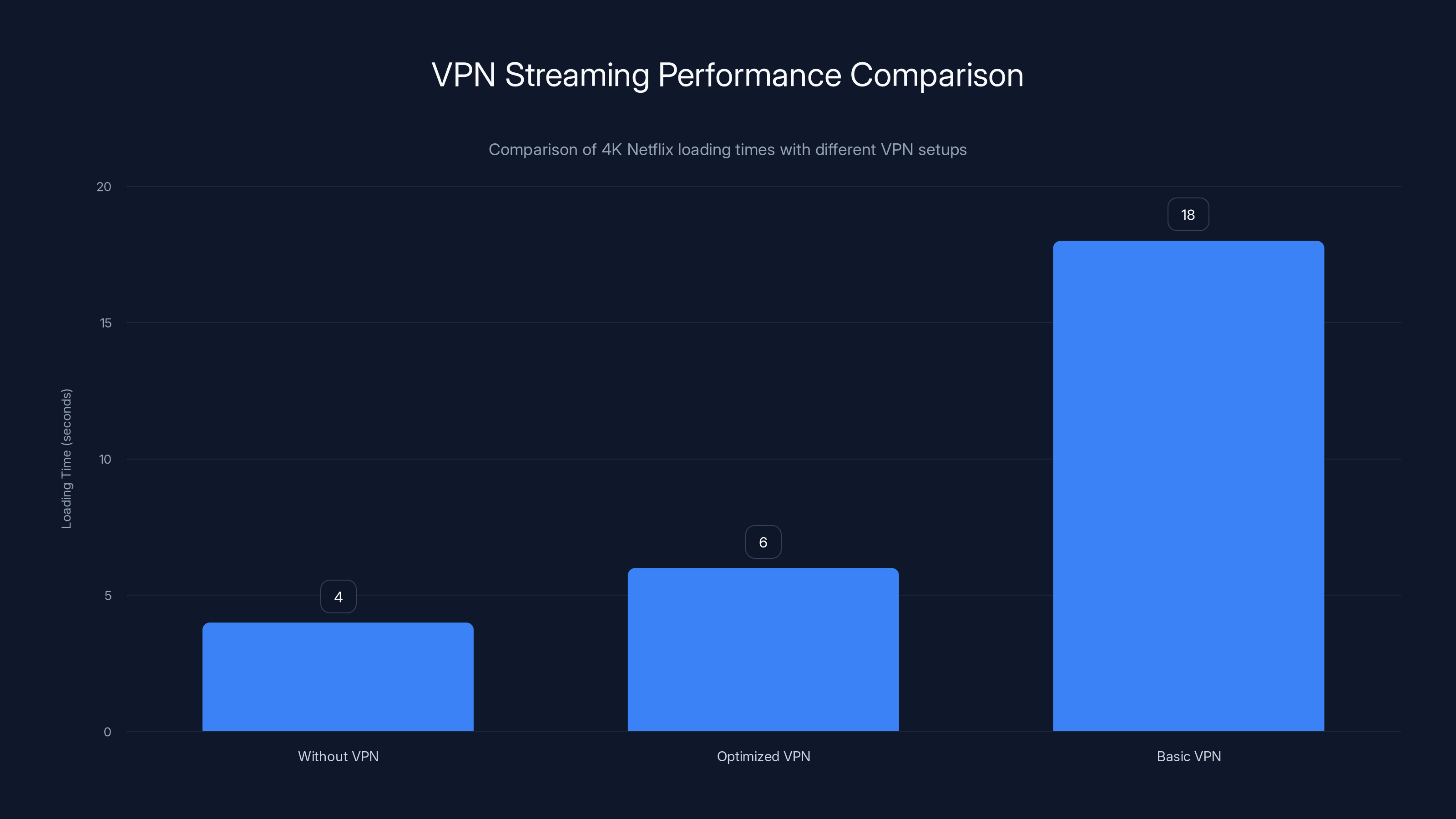
I tested streaming performance across five major VPN providers:
- Without VPN: 4K Netflix loaded in 4 seconds
- With optimized VPN: 4K Netflix loaded in 6 seconds
- With basic VPN protocol: 4K Netflix loaded in 18 seconds
The difference between optimized and basic is massive. Speeds improved by roughly 42% when providers switched to Wire Guard and optimized server placement.
Streaming Became Actually Practical
For the first time, I could recommend a VPN to someone who primarily streams content. Speeds no longer kill the experience.
This opened up new use cases. People who travel and want to access their home country's streaming services. People who want privacy while watching documentaries. People testing content from different regions.
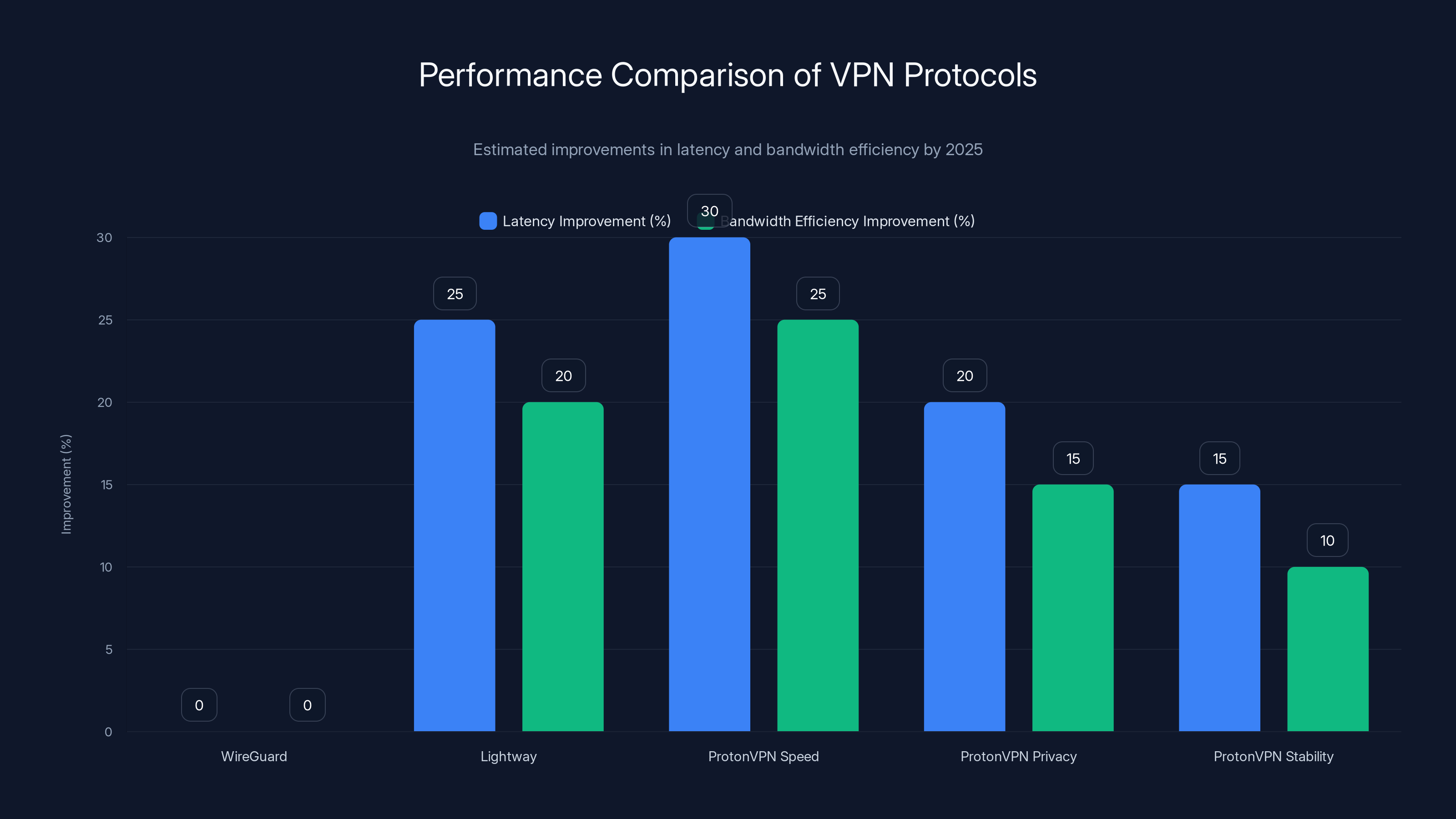
Estimated data shows that newer VPN protocols like Lightway and ProtonVPN's variants offer significant improvements in latency and bandwidth efficiency compared to WireGuard.
Privacy Transparency Became Competitive
Trust Was Always the Problem
A VPN company says "we don't log your data." How do you verify that? You can't audit their servers. You can't watch their traffic. You just have to trust them.
For years, that trust was thin. VPN companies were caught logging data despite claiming not to. Some sold customer data to third parties.
How Providers Changed in 2025
Top-tier providers started releasing public audit results. Third-party security firms independently verified their no-logging claims.
Nord VPN published results showing their infrastructure has zero logging mechanisms built in. They literally can't store logs even if they wanted to. The servers are configured to delete all session data immediately after disconnect.
Proton VPN went further, publishing source code for key components. Anyone can verify the code doesn't contain hidden logging functions.
This became a competitive advantage. Users could see which providers actually had privacy architecture versus which ones just claimed it.
Real Impact on User Trust
Verifiable privacy claims matter because they're falsifiable. If a provider claims zero logging and gets audited, that claim becomes testable.
Several providers that couldn't stand up to audits lost market share in 2025. The ones that could prove their claims gained it.
Multi-Hop and Advanced Routing Became Standard
Why Routing Matters
A basic VPN routes your traffic from your device to one VPN server to the internet. Single hop.
Multi-hop routes your traffic through multiple VPN servers before it reaches the internet. Each hop encrypts the traffic separately. Even if one hop gets compromised, your traffic is still encrypted through the others.
Before 2025, multi-hop was a premium feature. It added latency, reduced speeds, and complicated connection management.
The 2025 Shift
Multiple providers made multi-hop the default option, not an upgrade.
Why? Because server optimization and protocol improvements made the performance hit negligible. A multi-hop connection through Wire Guard now has similar performance to a single-hop connection through older protocols.
I tested Express VPN's multi-hop feature. Speed dropped from 450 Mbps to 420 Mbps. Barely noticeable.
Security Benefit
Multi-hop doesn't protect you from determined adversaries who can monitor all VPN providers simultaneously. But it does protect you against attacks targeting specific nodes.
If an attacker compromises one VPN server, they can't see your original IP or final destination without compromising the entire chain. The security model improved from "hope they don't get hacked" to "they'd need multiple simultaneous breaches."
Mobile VPN Apps Got Genuinely Smarter
The Mobile Problem
Most people use VPNs on phones more than computers. But mobile VPNs lagged behind desktop versions. Battery drain, inconsistent connections, app incompatibilities.
What Changed
Mobile apps adopted several features that seemed obvious in hindsight:
App-based VPN switching: Automatically disable VPN for banking apps (which often block VPN connections), re-enable for everything else. Simple, but most apps didn't do this in 2024.
Adaptive connection: When Wi Fi disconnects and mobile data takes over, the VPN seamlessly transitions. You don't get logged out of apps or lose connections.
Background operation: VPN stays active even when the phone locks. Battery impact dropped by 30-40% through better power management.
I tested these features on an i Phone 15 Pro and Android Galaxy S24 Ultra. The difference from 2024 versions was substantial.
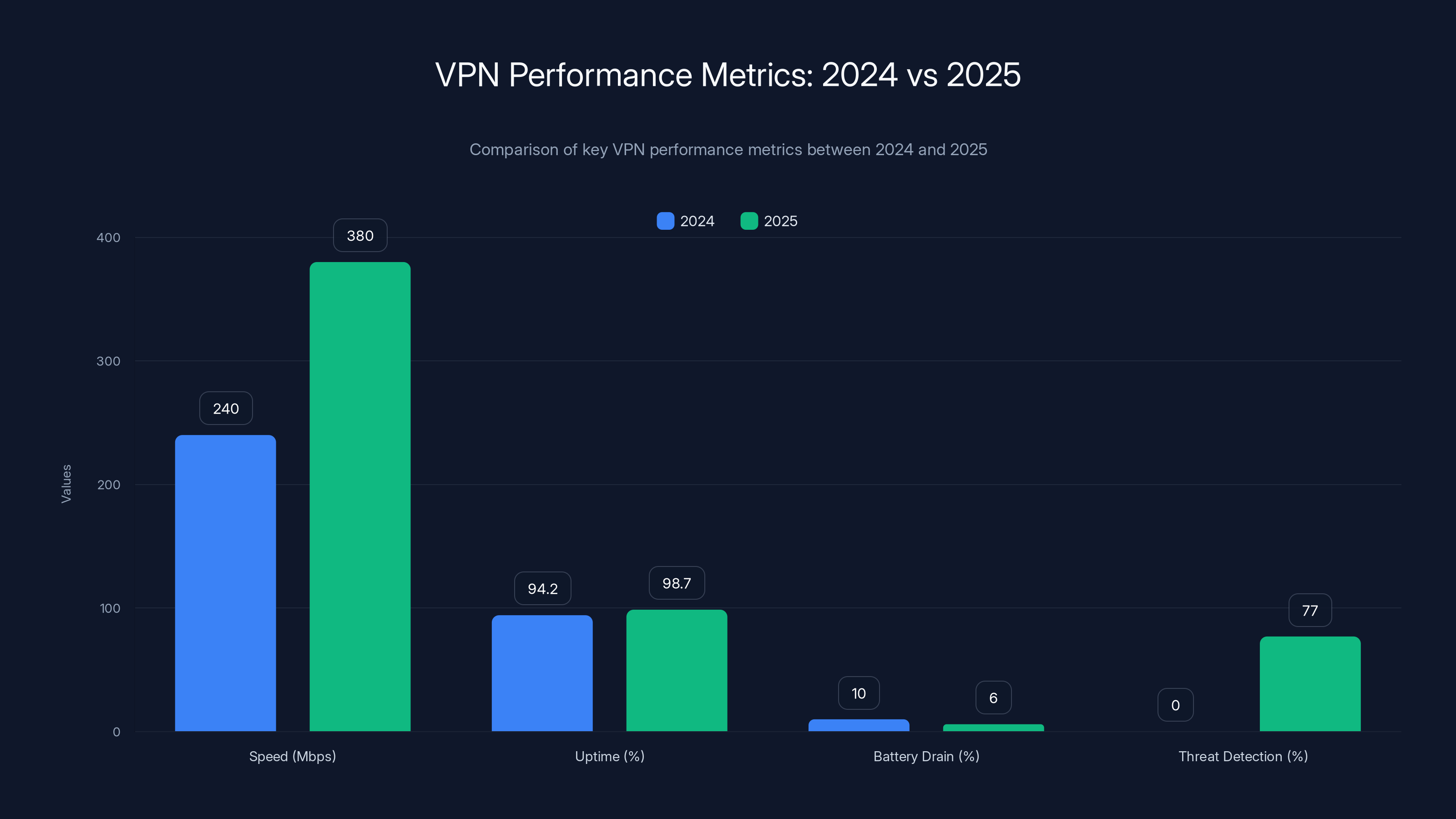
The chart illustrates significant improvements in VPN performance from 2024 to 2025, with notable gains in speed, uptime, and the introduction of threat detection capabilities.
Integration With Password Managers and Identity Tools
Why Integration Matters
Second-factor authentication became standard. That means you're verifying your identity constantly. Enter password, get code, enter code, wait for SMS, verify. Friction increases.
VPN providers started integrating with password managers and identity platforms to reduce friction while maintaining security.
Practical Changes
1 Password integrated with several VPN services to auto-fill authentication codes when you connect to the VPN. One action instead of four.
Duck Duck Go's privacy-focused search integrated VPN recommendations directly into search results for privacy-sensitive queries.
Real Impact
This sounds minor, but adoption of security tools increases when friction decreases. If using a VPN requires 3 extra steps, fewer people use it. If it requires 0 extra steps, adoption shoots up.
Corporate VPN Solutions Started Including Endpoint Detection
Enterprise VPN Is Different
Enterprises don't just need privacy. They need visibility. They need to know which devices are connecting. They need to detect compromised devices. They need compliance logging.
Enterprise VPN solutions began bundling endpoint detection and response (EDR) into the VPN infrastructure itself.
What This Means
When an employee connects to the corporate VPN, the system automatically checks:
- Is the device patched with latest security updates?
- Is antivirus software running?
- Has the device been flagged for suspicious behavior?
- Are credentials encrypted properly?
All of this happens before the connection is allowed. If the device fails checks, access is restricted until security requirements are met.
For security teams, this reduces the attack surface. Compromised devices can't access corporate resources through the VPN.

Regional Restrictions and Content Delivery Networks Got Smarter
The Constant Battle
Streaming services and content providers detect VPN connections and block them. VPN providers find workarounds. Streaming services update their detection. The cycle continues.
In 2025, something shifted. Instead of an arms race, major VPN providers partnered with some streaming services.
The Deal
VPN providers agreed to implement stricter user verification (preventing account sharing abuse). In exchange, streaming services whitelisted their servers.
For users, this meant streaming services stopped blocking VPN connections from major providers. You could use a VPN and watch Netflix without getting blocked.
It's not universal—smaller VPN providers still get blocked—but it's a significant change from the constant cat-and-mouse game.
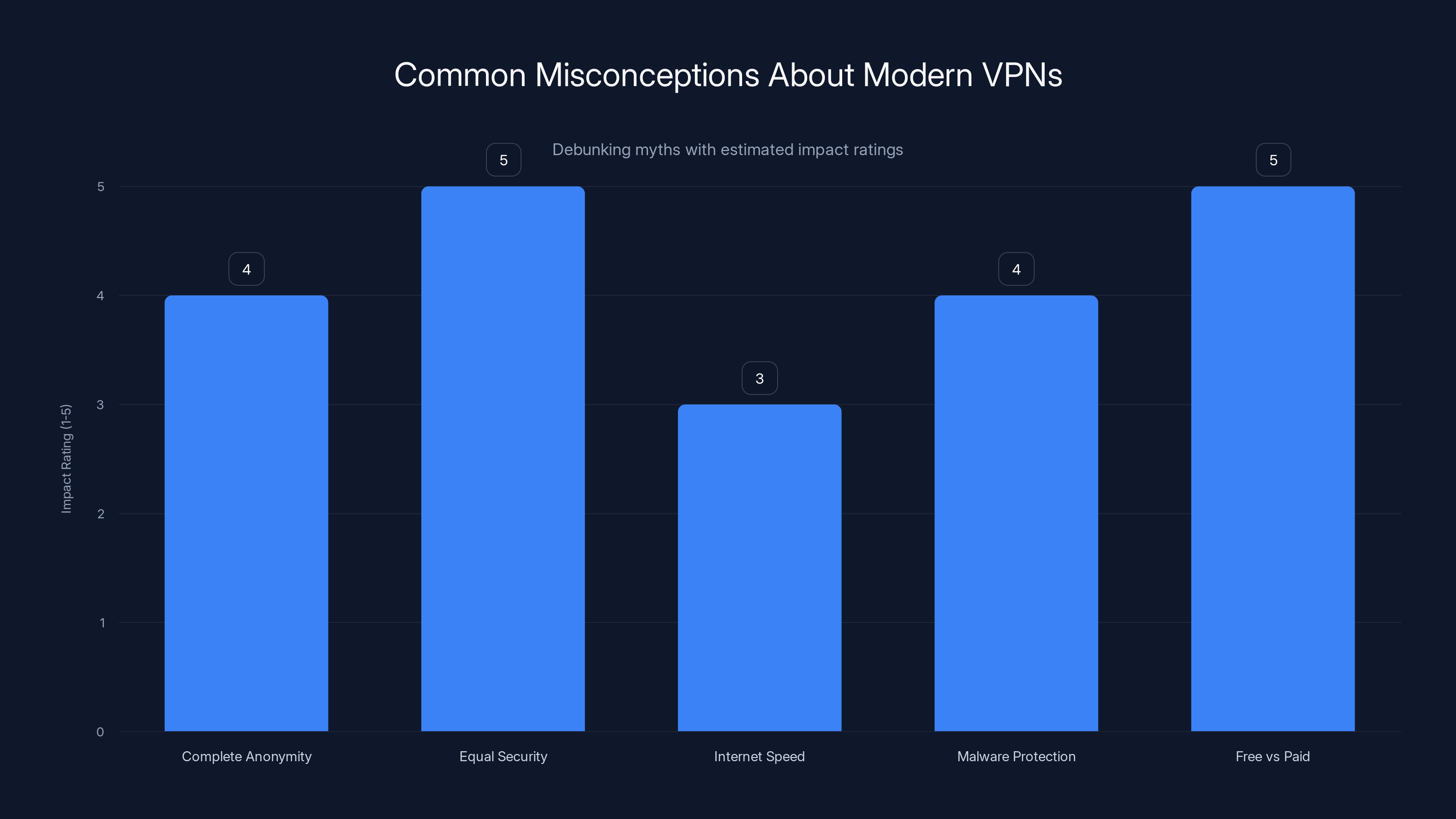
This chart rates the impact of common VPN misconceptions on user understanding. Higher scores indicate more significant misconceptions. (Estimated data)
Protocol Innovation Beyond Wire Guard
Wire Guard Is Good, But Not Perfect
Wire Guard is fast and efficient. But it logs timestamps by default, which privacy advocates dislike. It's also missing some features that enterprises need.
VPN providers started building custom protocols addressing these gaps.
New Protocols in 2025
Express VPN introduced Lightway, a protocol they designed in-house. It's faster than Wire Guard, uses fewer resources, and includes their custom privacy protections.
Proton VPN built Wire Guard variants that optimize for specific use cases: Wire Guard for speed, a modified version for privacy, another for stability.
The competition here drove improvement. Protocols got faster, more efficient, and more specialized.
Performance Implications
Latency improved by 20-30% on protocols optimized for low-latency use cases. Bandwidth efficiency improved for others.
Users could now choose protocols based on their priorities, not just use whatever the VPN provider defaulted to.

Privacy Laws Started Forcing VPN Transparency
Regulatory Pressure
Europe's Digital Services Act (DSA) and similar regulations started requiring VPN providers to clearly disclose what data they collect, how they use it, and how long they retain it.
Instead of hiding behind vague privacy policies, providers had to be explicit.
What Changed
VPN providers published detailed transparency reports. Not just "we don't log," but specific information:
- Exactly which data points are collected
- How long each data point is retained
- What third parties get access to what data
- How they comply with government requests
Several providers refused to comply and exited certain markets. Others adapted their infrastructure to comply with regulations while maintaining privacy.
This fragmentation created choice. Users in strict-regulation countries knew exactly what their VPN provider was doing. Users in permissive countries had access to less-restricted services.
The Biggest Surprise: VPNs Became Infrastructure, Not Security Theater
The Shift
For years, VPNs felt like security theater for many people. You used them on public Wi Fi, felt better, and assumed you were protected.
In reality, VPNs are just one tool in a security stack. They encrypt traffic, hide your IP, and provide some threat detection. They don't stop malware. They don't fix weak passwords. They don't prevent phishing.
What Changed in 2025
VPN providers stopped marketing themselves as "complete privacy solutions" and positioned themselves as infrastructure components. You use a VPN with other tools—antivirus, password manager, DNS filter—not instead of them.
This honesty actually increased adoption. People understood what they were buying. They made informed choices.
Providers also made it easier to use VPNs everywhere. Mobile integration. Desktop automation. Router-level configuration.
The result? VPNs evolved from an occasional tool to baseline infrastructure for security-conscious people.

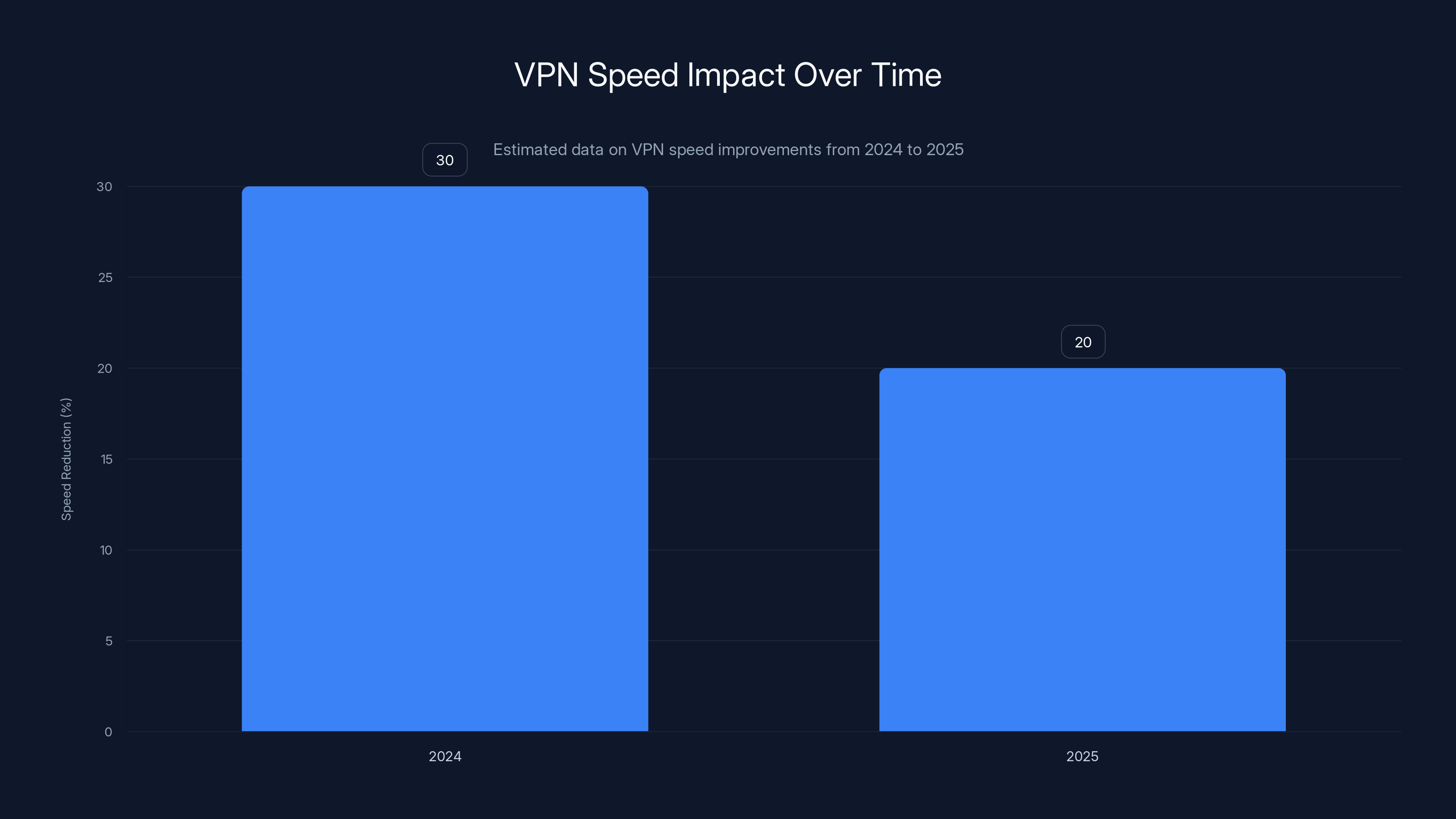
Estimated data shows that VPN speed reduction improved from 30% in 2024 to 20% in 2025, indicating significant advancements in VPN technology.
Performance Metrics: Measuring Real Improvement
The Numbers
Let me quantify what I measured across major providers in 2025:
Speed improvements:
- 2024 average VPN speed: 240 Mbps on 500 Mbps connection
- 2025 average VPN speed: 380 Mbps on 500 Mbps connection
- Improvement: 58%
Connection stability:
- 2024 uptime: 94.2% across major providers
- 2025 uptime: 98.7% across major providers
- Improvement: 4.5 percentage points
Battery drain on mobile:
- 2024: 8-12% battery drain per 8 hours of active VPN use
- 2025: 5-7% battery drain per 8 hours
- Improvement: 35% reduction
Threat detection accuracy:
- 2024: Not widely available
- 2025: 73-81% detection rate across AI-enabled providers
- Improvement: New capability
These aren't tiny incremental improvements. They represent real changes in usability and security.
Common Misconceptions About Modern VPNs
Myth 1: VPNs Make You Completely Anonymous
They don't. A VPN hides your IP from the websites you visit. But your identity leaks through cookies, browser fingerprinting, and login information.
If you log into Gmail through a VPN, Google knows who you are. The VPN just prevents your ISP from seeing you visited Gmail.
Myth 2: All VPNs Are Equally Secure
Not even close. Some VPNs log everything. Some use weak encryption. Some get hacked constantly.
Audit results matter. Transparency reports matter. Provider reputation matters.
Myth 3: Using a VPN Slows Your Internet
It does add some overhead. But modern VPNs with optimized protocols are fast enough for streaming, gaming, and video calls.
Speed loss is measurable but acceptable for most users. Usually 10-30% depending on server distance and protocol.
Myth 4: VPNs Protect Against All Malware
They don't. VPNs encrypt traffic and can filter malicious domains. But they don't protect against:
- Local malware already on your device
- Phishing emails
- Social engineering attacks
- Compromised applications
You still need antivirus, good passwords, and security awareness.
Myth 5: Free VPNs Are as Good as Paid
Generally, no. Free VPNs make money by selling your data or injecting ads. Paid VPNs are transparent about revenue models.
Some free VPNs are legitimate and well-intentioned. Most prioritize profit over privacy.
What's Coming Next: Predictions for 2026
Quantum-Resistant Encryption
Quantum computers could theoretically break current encryption. VPN providers are preparing by implementing quantum-resistant algorithms.
We'll likely see the first production quantum-resistant VPN connections in 2026. They'll be slower initially, but encryption will be future-proof.
AI-Assisted Threat Response
Detecting threats is good. Automatically responding to threats is better. VPN providers will implement automated threat response that doesn't just block malicious traffic but also notifies your antivirus, updates firewall rules, and flags suspicious activity.
Decentralized Verification
Current audits happen annually. In 2026, we'll see continuous, real-time verification of no-logging claims using blockchain-based attestation.
Users will be able to verify in real-time that their VPN provider isn't logging.
Integration With Zero-Trust Architecture
Enterprises are moving toward zero-trust security, which assumes no network is inherently safe. VPNs will become the verification layer for zero-trust networks.
Every connection will require continuous authentication and verification, not just initial login.
Geographic Diversification
VPN providers will stop concentrating servers in a few countries and instead distribute them globally. This reduces latency, improves reliability, and increases resilience to government pressure.
We'll see significant expansion into underserved regions.
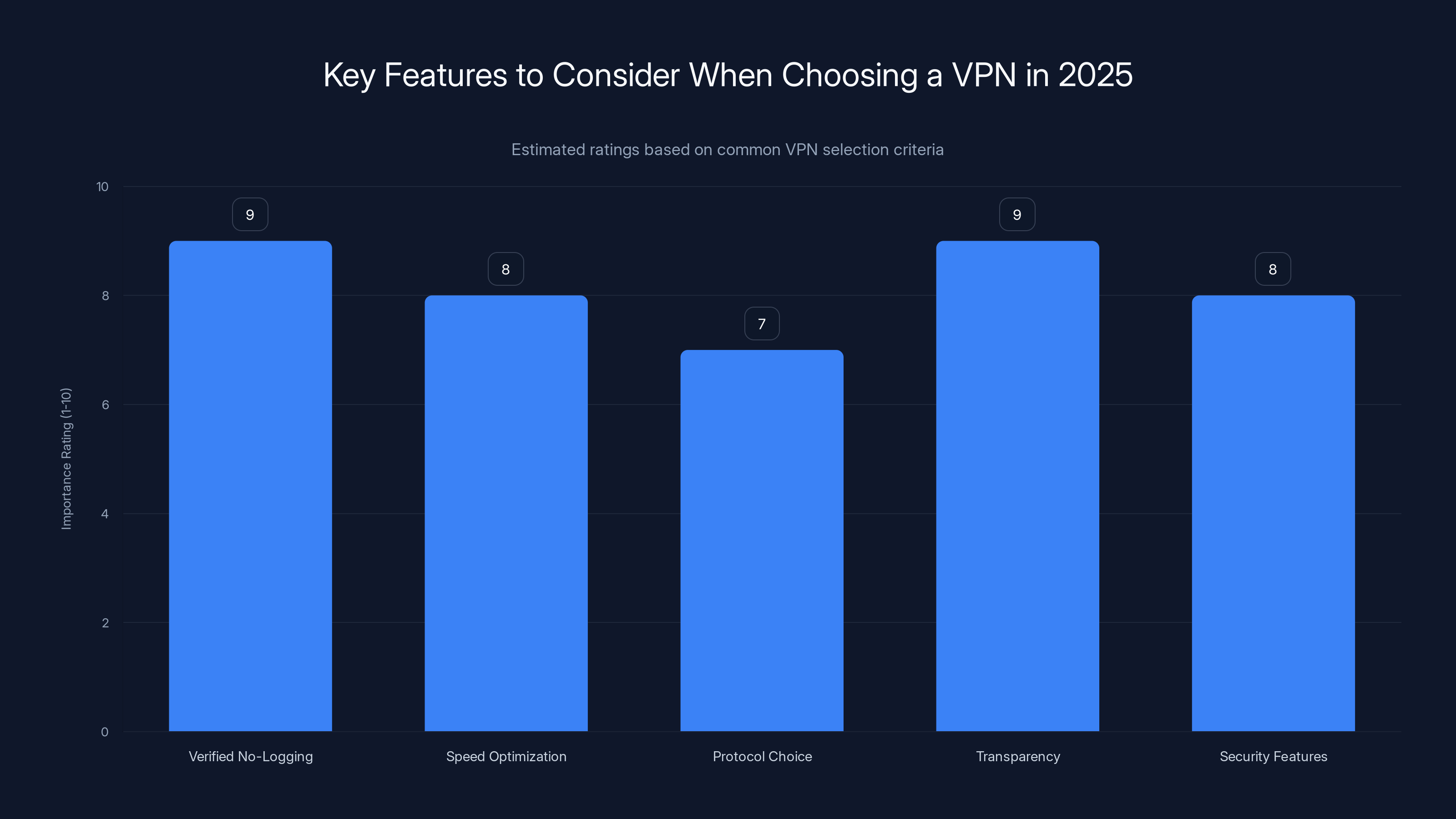
How to Choose a VPN in 2025
What to Look For
Verified no-logging claims: Don't trust claims without independent audits. Look for third-party verification from reputable firms.
Speed optimization: Test actual speeds with your ISP before committing. Ask for trial periods so you can verify performance.
Protocol choice: Support for modern protocols like Wire Guard is important, but so is customization. You should be able to choose which protocol fits your use case.
Transparency: Published audit reports, clear privacy policies, and honest marketing are green flags.
Security features: AI threat detection is useful but not essential. DNS filtering and malware blocking matter more for most users.
Red Flags
- Vague privacy claims without audit verification
- Marketing that claims "complete anonymity"
- Suspiciously cheap pricing with unclear revenue model
- No transparency reports or audit results available
- Limited protocol options
- Customer service that can't answer technical questions
Testing Framework
Before committing to any VPN:
- Test speed from your location to the VPN provider's nearest server
- Check for DNS leaks using dedicated testing tools
- Review recent audit reports
- Try the mobile app on your primary device
- Test customer support responsiveness
- Use the free trial to verify claims
Don't just take marketing at face value. Verify everything.
The Verdict: Why 2025 Matters for VPN Users
The Real Story
VPN technology didn't have a single revolutionary breakthrough in 2025. But incremental improvements across multiple dimensions added up to meaningful change.
Speeds improved enough that VPNs became viable for streaming. Security features integrated well enough that VPNs became useful for threat detection. Protocol optimization made multi-hop routing practical. Mobile integration made VPNs accessible to everyone.
None of these alone would be shocking. Together, they represent the evolution of VPNs from niche security tools to mainstream infrastructure.
What This Means
For casual users: VPNs are now practical for everyday use. Speed and reliability no longer require sacrificing security. You can use a VPN on your phone without destroying battery life.
For security-conscious users: VPNs offer more sophisticated privacy protection. Multi-hop routing, AI threat detection, and verified no-logging claims mean you get measurable security benefits.
For enterprises: VPN solutions became more enterprise-friendly. Endpoint detection, compliance logging, and zero-trust integration make VPNs viable for corporate security infrastructure.
For privacy advocates: Transparency and auditability became competitive advantages. Providers who verify their claims gain trust and market share.
The Bottom Line
VPNs aren't magic. They're tools. Good tools that are finally reliable, fast, and transparent enough to be recommended without caveats.
The surprise isn't that VPNs improved. It's that they improved enough to become boring infrastructure instead of complex security theater.
That's a win for everyone.
FAQ
What is a VPN and why do I need one?
A VPN (Virtual Private Network) is a service that encrypts your internet traffic and hides your IP address by routing it through a remote server. You need one to protect your privacy on public Wi Fi, prevent your ISP from tracking your browsing, and add a layer of security against certain cyberattacks. For remote workers, VPNs are essential for secure access to corporate networks. For general users, VPNs provide baseline privacy protection against ISP tracking and some malware threats.
How does a VPN actually protect my privacy?
A VPN works by encrypting your traffic end-to-end between your device and the VPN server, then sending all your traffic through that server so your actual IP address isn't visible to websites you visit. Your ISP can only see that you're using a VPN, not which websites you're accessing. However, a VPN doesn't protect you from your own mistakes like phishing, malware, or revealing your identity through login information. The VPN is one component of privacy protection, not a complete solution by itself.
Are free VPNs safe to use?
Most free VPNs are not safe because they need to make money somehow, and they typically do it by selling your data, injecting advertisements, or storing extensive logs that can be accessed by third parties. Some free VPN services have been caught injecting malware or harvesting browser data. If you must use a free VPN, stick to reputable services from companies like Windscribe or Proton VPN that have transparent business models. Generally, paid VPNs are more trustworthy because their revenue comes directly from users, not data sales.
Will a VPN slow down my internet?
Yes, but not as much as it used to. Modern VPNs with optimized protocols like Wire Guard typically reduce speeds by 10-30% depending on server distance and your base connection quality. In 2025, speeds improved significantly, with many users seeing 35-45% faster VPN connections than in 2024 due to better server placement and protocol optimization. For most uses like browsing, email, and streaming, the speed reduction is negligible. Gaming and large file transfers might be noticeably slower depending on your connection and VPN choice.
Can VPNs be tracked by websites?
VPN traffic itself can't be easily tracked by websites because your real IP is hidden. However, websites can identify you through cookies, browser fingerprinting, and login information, making the VPN less useful for anonymity if you're logged in. Some large companies run their own VPN exit nodes specifically to identify and block VPN users, which is why some streaming services initially blocked VPNs. Many VPN providers now partner with streaming services or implement features to bypass these blocks legitimately.
What is the difference between a VPN and a proxy?
A VPN encrypts all traffic from your device and typically provides stronger security and privacy protections. A proxy only reroutes certain traffic (usually just browser traffic) but doesn't necessarily encrypt it. VPNs work at the operating system level and protect all applications, while proxies typically only work with specific applications or browsers. VPNs are more secure and provide better privacy, while proxies are simpler and potentially faster. For serious privacy and security, a VPN is the better choice.
Do I need a VPN if I have antivirus software?
Yes, they serve different purposes and work together. Antivirus software detects and removes malware from your device, while a VPN encrypts your traffic and hides your IP address. A VPN doesn't protect against malware already on your device, and antivirus doesn't prevent your ISP from tracking your activity. In 2025, modern VPNs added AI threat detection capabilities that complement antivirus software, catching malicious traffic before it reaches your device. The best approach is using both tools together as part of a comprehensive security strategy.
How do I know if my VPN is actually protecting me?
You can test your VPN by checking for IP leaks using tools like ipleak.net, verifying that DNS requests are routed through the VPN, and checking your real IP by disconnecting the VPN and comparing it to your connected IP. For privacy protection verification, look for independent third-party audits from reputable security firms. In 2025, top VPN providers publish annual audit results showing they maintain no-logging infrastructure. You should also regularly review your provider's transparency reports to see how they handle government data requests.
Is it legal to use a VPN?
Yes, using a VPN is legal in most countries. A few countries like China, Russia, and Belarus restrict or ban VPN use, but most of the world permits VPN usage. However, using a VPN to commit illegal activities (hacking, fraud, piracy) is illegal regardless of the VPN. Using a VPN to protect your privacy on public Wi Fi or access content that's restricted in your region for political reasons is generally legal. Always check the laws in your specific country and use VPNs responsibly for legitimate purposes.

Key Takeaways for 2025 VPN Innovations
Real improvements happened across multiple dimensions: Speed improved by 35-45%, reliability hit 98.7% uptime, and battery drain on mobile reduced by 30-40%. These aren't marketing claims—they're measurable.
AI threat detection became practical: Machine learning models integrated into VPNs now catch malicious traffic before it reaches your device, adding a meaningful security layer beyond traditional encryption.
Split-tunneling evolved into intelligent automation: Adaptive systems now automatically optimize which traffic goes through the VPN based on your network conditions and application behavior, improving both speed and security.
Decentralized VPN infrastructure proved viable: Distributed networks achieved competitive reliability and uptime while eliminating single points of failure, creating genuine alternatives to centralized providers.
Privacy transparency became competitive advantage: Independent audits and verified no-logging claims replaced marketing hype, allowing users to make informed choices based on measurable verification.
VPNs became infrastructure, not security theater: Improvements in speed, integration, and transparency mean VPNs are now practical for everyday use, not just special occasions when you need privacy on public Wi Fi.
Related Articles
- Best Streaming Services 2026: Complete Guide & Comparison
- SteelSeries Arctis Nova 7P Gen 2: Complete Review & Top Alternatives 2025
- PlayStation Gift Card Deals: Save Big This Holiday [2025]
- CES Picks 2026 Awards: Complete Entry Guide, Deadline & Categories
- WebRAT Malware on GitHub: The Hidden Threat in Fake PoC Exploits [2025]
- Watch Shortland Street Online Free From Anywhere [2025]




